Webhooks
Overview
In response to some events, we generate and send out a webhook message to your defined URL.
All ClearBank webhooks consist of a
DigitalSignature,Type,Version,PayloadandNonce.Payloadparameters vary depending on the webhook. Webhook responses contain a 200 HTTP status code which includes aNoncenumber in the body and yourDigitalSignature.
Anatomy of a webhook
| Element | Type | Description |
|---|---|---|
DigitalSignature | string | ClearBank®'s Digital Signature |
Type | string | The type of the event |
Version | int | The webhook version |
Nonce | int | Cryptographically secure number generated by ClearBank® for every single webhook. A nonce number is generated randomly and should not be used as a check for duplication |
Payload | array[object] | Object which contains information related to the webhook |
Response
| Element | Type | Description |
|---|---|---|
DigitalSignature | string | Signed hash of the body of the request. The hash signed by your private key |
Nonce | int | The value that you receive in the webhook |
200 | int | HTTP response status code |
Responding to a webhook
The webhook sent by ClearBank® acts as a verification mechanism.
You verify that it is ClearBank® that has sent you the webhook and subsequently, ClearBank® needs to verify that you have successfully received the webhook (based on your response acknowledging receipt).
This verification occurs when you return a 200 HTTP response, which includes the Nonce number in the response body and your DigitalSignature.
If your response is invalid, we will consider it as a failed webhook.
ClearBank® will send the webhook every 15 minutes for 24 hours unless a successful response is returned by you.
To verify the integrity of the webhook received from ClearBank®:
- Download a Public Key that is specific to your institution by clicking the Download Public Key button on the Webhook Management page of the Institution portal.
- Hash the request body using
SHA 256 - Convert the
DigitalSignatureRequest Header value fromBase64encoded string into the byte array - Verify the signature using the
RSAalgorithm
To create the webhook digital signature:
- Take the Nonce number from the webhook and place it in the body of the response (e.g.
{"nonce": <value>}) - Hash the response body using
SHA 256 - Sign the hash with your
Private Keyand attach the signed hash asBase64encoded in theDigitalSignatureResponse Header
Your Private Key needs to correspond to a Public Key which has been used to create a Certificate Signing Request (CSR). Please refer to creating your authentication profile for more information.
Example HTTP request:
POST http://yourdomain.com/sample/webhook HTTP/1.1Content-Type: application/jsonContent-Length: 72Digitalsignature: YYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYX-Request-Id: f0309d95-4f68-4ecd-9c8d-b2d08d9fedd8{"Type":"FITestEvent","Version":1,"Payload":"test me","Nonce":1448545215}
Example HTTP response:
HTTP/1.1 200 OKDigitalsignature: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXContent-Type: application/json{"Nonce": 1448545215}
Setting up and testing webhook listener URLs
You can create one webhook listener for all events or separate webhook listeners specific to an event.
In this example, you will setup an FITestEvent webhook URL, which you can test against the TEST POST endpoint.
To manage your webhook definitions and set your webhook listener URLs for each event:
- Log in to the Institution Portal. More information about accessing the portal can be found here.
- From the menu, select Institution > Webhook Management.
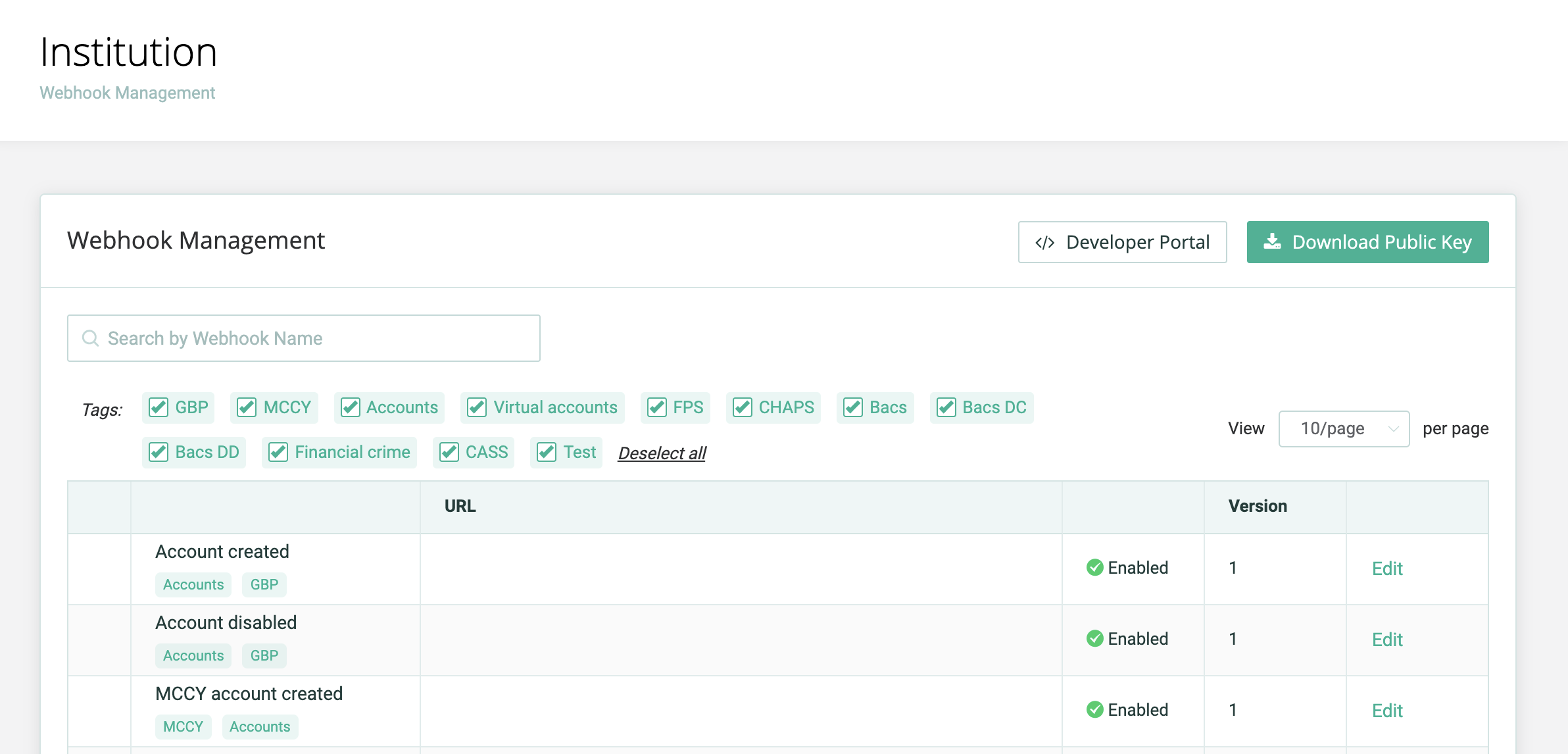
- Search for Test webhook and click the Edit button.
- Enter the URL you want to define as your webhook listener for this webhook and set the webhook status to Enabled.
- Click Save to successfully setup the webhook listern URL.
- To test the webhook, click the Test button.
- Enter a test message in the Test webhook window for example, ‘Hello World’ and click Send.
You should receive a FITestEvent webhook to your nominated URL and it should contain the test message in the body.
You must not include any sensitive information (such as API keys) in your webhook URLs.
The range of public IP addresses to support your interaction with ClearBank® webhooks are:
- Simulation Public IP address range:
51.145.122.16/28 - Production Public IP address range:
51.145.122.32/28
Accounts
Associated Endpoint
Webhook
Virtual Accounts
Associated Endpoint
Webhook
Multicurrency Accounts
Associated Endpoint
Webhook
Associated Endpoint
Webhook
Associated Endpoint
Webhook
Associated Endpoint
Webhook
Multicurrency Virtual Accounts
Associated Endpoint
Webhook
Associated Endpoint
Webhook
Associated Endpoint
Webhook
Associated Endpoint
Webhook
Multicurrency Statements
Associated Endpoint
Webhook
Associated Endpoint
Webhook
Payments
Associated Endpoint
Webhook
You may occasionally receive multiple webhooks with the same EndtoEndTransactionId. In this instance, a duplicate check should take place using the TransactionId.
If the same TransactionId is used for both payments, the webhook will be a duplicate. In case the TransactionId(s) are different, these will relate to separate transactions.
A full list of webhook documentation is available on ClearBank®'s Knowledge Centre and access can be granted as part of your onboarding journey. Please reach out to your main contact ClearBank® for more information.
High Value International Payments
Internal Transfers
Associated Endpoint
Webhook
FX Trade
Associated Endpoint
Webhook